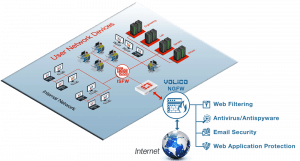
Data security remains the most critical cybersecurity issue on the map today. It’s now standard to employ some firewall type on every system, most commonly a next-generation firewall (NGFW). However, another multipurpose option is available: a unified threat management (UTM) appliance.
With the increasing need for more secure and reliable systems, many companies seek high-end solutions to protect their data and avoid downtime due to cyber threats. However, many are puzzled by the solution they found out there on the market, and it makes it difficult to decide which solution is best suited for your needs. Therefore, choosing between next-generation firewall or unified threat management could help understand what each security solution offers.
We are here to strip down the precise differences between two terms that are often used interchangeable next-generation firewall and unified threat management—and help you determine which option will offer better protection for your sensitive user information and critical private data.
The Purpose Of A Firewall
A firewall is one of the most vital pieces of defense your business has against digital threats. You can view your firewall as the gatekeeper between the organization’s servers and the outside world. If your firewall is maintained correctly, it will protect your servers from external threats and deal with more subtle problems by alerting you and intercepting ongoing data. A firewall paired with an anti-malware suite can save your business from cyberattacks and virus infection that could lead to significant revenue loss if not dealt with in time.
Connecting your computer to the world-wide-web is like leaving your front door open and allowing outsiders to get in. That is why the firewall is essential because it acts as the doorkeeper. The firewall is a piece of software that stands between your computer or network and the Internet. In other words, firewall software is installed with the intention of scanning every incoming and outgoing packet of data, checking for malicious or inappropriate content, and then allowing or denying the packet of data entry into the system.
Without a firewall, any request will pass through to vulnerable systems, making it possible for malicious actors to access your computer for their own gain. A firewall blocks unauthorized requests and allows passage only to designated traffic. There are a couple of functions used by the firewall to ensure your servers’ safety, and we will briefly go through them.
Filtering
One of the most important aspects of a firewall is the filtering option. As the computer sends a request across the internet, it takes the form of a packet of data that travels through the network until it reaches its destination. The targeted server sends a response back to the computer in the same format and along the same route. Firewalls monitor all the data packets that pass through, and it takes into account it’s content, the source, and the destination.
During the monitoring process, the firewall compares the information to its internal rule, and if it detects an unauthorized package, it discards the data. Typically, firewalls will allow web browsers, email, and other common programs while discarding other incoming requests.
Logging
The firewall’s ability to log any incoming traffic is also an important feature. By monitoring multiple packets of data, the firewall can create a clear picture of the kind of traffic your system experiences. With this feature, the firewall can be valuable in identifying the source of external threats, and it can also be used to monitor other system users’ activity.
Internal Threats
Even though we mostly talked about the external attacks, some of the threats might come from inside. Your firewall serves the valuable purpose of monitoring ongoing connections. Some malware types will send signals once they take over the system, allowing malicious actors to take specific actions or take over the computer remotely. A firewall can alert you of unknown program attempts or possible malware infection, allowing you to shut down the system and prevent further damage.
Some of the next-generation firewalls can be software or hardware-based and go even further than simply assessing and acting on data packets; they include many other functions to help defend the network, including:
- Stateful inspection
- Application awareness
- Active Directory or LDAP identification
- A fully integrated intrusion protection system
- Bridged or routed modes available
What is a Unified Threat Management (UTM) appliance?
A Unified Threat Management provides a wide array of security features in a single device or service on the network. The functions included in UTMs include anti-spam, content filtering, web filtering, and anti-virus. You can view a UTM system as a type of network hardware appliance, virtual appliance, or cloud service that protects your systems from threats in a very simplified way. UTMs combine and integrate multiple services and features into a converged platform of point security products.
UTM systems are suited for small and midsize businesses, and most of its features fall under three large categories: intrusion/firewall prevention system(IPS)/virtual private network, messaging security (anti-spam, mail AV) and anti-virus, secure web gateway security(Web anti-virus and URL filtering)
We mentioned that NGFW could be either software or hardware-based, but UTM appliances are always hardware. This brings advantages and disadvantages. A minor disadvantage of a UTM appliance is that, in order to function, it needs to be connected to the main network. The advantages of a UTM appliance are the wide array of functions it can perform from that position:
- Load balancing for the network
- Avert data leaks
- Data loss prevention
- Gateway antivirus prevention
- Gateway anti-spam
- Network intrusion detection and prevention
- Appliance reporting
- Email security
- URL filtering
- Content filtering
- Wireless security
- Virtual private network termination
- Web application firewalls
- DDOS mitigation
- Reduced compliance burden
- Continual automatic updates
- Accelerated performance
What this list of utilities means is that, essentially, a UTM appliance incorporates all the functions of an NGFW on top of a critical array of uses. It is possible to get all these services from myriad vendors and applications. However, the advantage of a UTM appliance is that all the data is centralized and can be viewed holistically, providing a better overview of real-time network threat detection status. Various UTM brands will offer even more specialized tasks.

Choosing The Right Option For Your Needs
The concepts present substantial differences, and some might find it confusing or hard to understand. However, many writers and supplies argue that there is no difference in practice between UTM and NGFW. Some of the main challenges faced by UTMs were solved as the technology matured and it was able to support the system in large environments.
Other opinions might point towards some differences between the two security solutions. Some might argue that NGFW is more suited for high-intensity traffic environments like telecommunications, complex businesses, and many other facilities that centralize large amounts of data traffic. However, some of these complex infrastructures might require you to separate security assets for the environment’s scalability and resilience.
In that case, some might recommend using UTM Firewall for small to medium-sized businesses where the data flow is lower. Regardless of the terminology used, it is crucial during the process of purchasing a perimeter security solution to analyze if the resources offered to meet the functional and growth requirements of the environment.
Conclusion
 Given that both an NGFW and UTM appliance perform the same essential functions, there isn’t a wrong answer to this question. Even many knowledgeable IT professionals use the two terms interchangeably. The price range on either purchase even tends to fall within the same general range. Ultimately, the decision should be based on whether you need the extra services a UTM offers over an NGFW since the NGFW is incorporated within the UTM appliance. More protection, provided you have the wherewithal to monitor and respond to the information generated, is always beneficial, as is staying ahead of incoming cybersecurity threats.
Given that both an NGFW and UTM appliance perform the same essential functions, there isn’t a wrong answer to this question. Even many knowledgeable IT professionals use the two terms interchangeably. The price range on either purchase even tends to fall within the same general range. Ultimately, the decision should be based on whether you need the extra services a UTM offers over an NGFW since the NGFW is incorporated within the UTM appliance. More protection, provided you have the wherewithal to monitor and respond to the information generated, is always beneficial, as is staying ahead of incoming cybersecurity threats.
With Volico Data Centers, you have access to a comprehensive IT security solution that guards your system against hostile intrusions. Their security services include all the features of a high-end managed security solution that will ensure the safety of your data and network connections.
Ready to see how a UTM appliance or NGFW from Volico can dramatically improve threat management for your IT services?
To find out more about cybersecurity options, have one of our friendly security experts contact you to begin the conversation. Discover how Volico can help you with your Managed Security needs.
• Call: 888 865 4261
• Chat with a member of our team to discuss which solution best fits your needs.