Meeting Regulatory Requirements Effortlessly With Bare Metal Servers Compliance

For strictly regulated industries, there’s nothing more important than ensuring that data is safe and secure. Data security and compliance are the first concerns for organizations in regulated sectors like healthcare and finance. These industries often require high-performance infrastructures, granular control, and enhanced data security, and this brings bare metal servers into the spotlight. Unlike […]
The Growing Importance of Data Center Governance
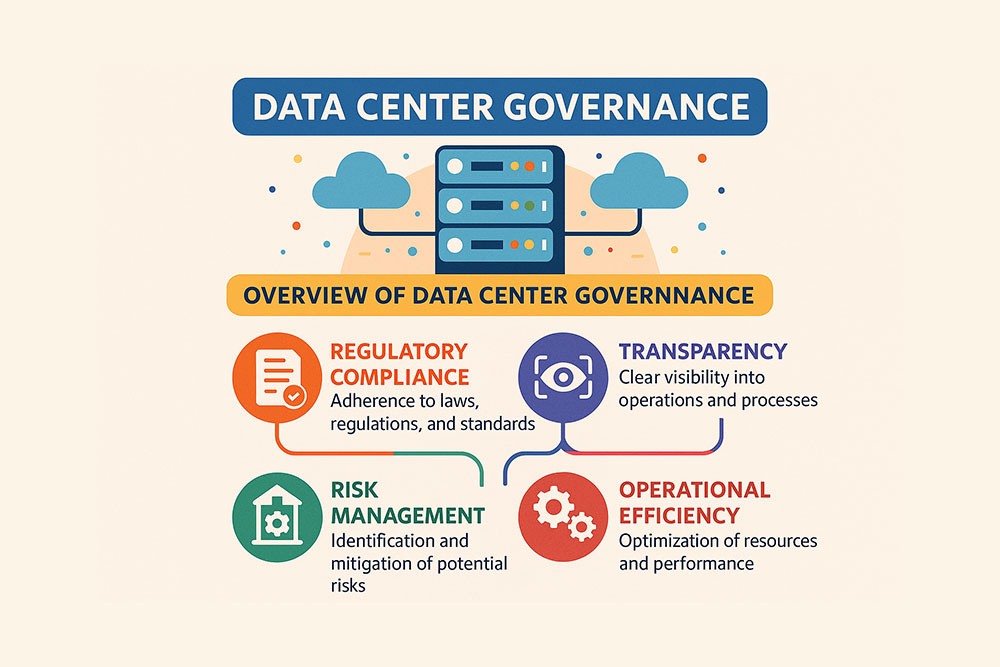
Data center governance is a term that doesn’t ring as many bells as the similar “data governance” does. Nevertheless, its importance, driven by the need for enhanced security, compliance, operational efficiency, and the ability to handle growing data volumes, is undeniable. Managing the exponential growth of business data requires robust governance strategies. As the cost […]
Understanding the Importance of Data Backups and Encryption for Businesses

Today’s business landscape is repeatedly disturbed by the devastating fallout of cyberattacks and data breaches. Even well-prepared companies with stringent security measures often find themselves astonished and confused when an unexpected attack happens, leading to data loss. Cybercriminals understand the value of business data. With their tools and practices becoming more and more advanced, organizations […]
How Data Center Automation Improves Operational Efficiency

The data center industry has seen significant growth in the last few years. Data volumes have increased dramatically, asking for better storage and processing. Data centers and AI have started to merge, requiring significant transformations worldwide. For many operators, implementing data center automation was a key solution to improve operational efficiency and maintain the quality […]
Why Bare Metal Servers Are Popular Again?

Bare metal servers are making a strong comeback, and if you’re responsible for IT infrastructure, you may be wondering whether your organization should get on this train. Virtualized environments can be great for specific workloads, however, VMs do have to share resources, which puts bare metal servers in a more special position. Unlike virtualized environments […]
SOC 2 Type 1 vs. SOC 2 Type 2 Compliance: Which Type Does Your Business Need?

Organizations today are increasingly relying on multiple different service providers for their many different needs. We have IaaS providers and SaaS providers to cover everything from email and payment processing to web hosting and a multitude of other needs. But how can you tell if a specific service provider is going to handle your organization’s […]
Colocation Security Advantages: Data Protection Strategies and Practices

Today, when data availability is becoming as natural as breathing, and our lives are impregnated in almost every aspect with technology, data security is among the first concerns for everyone. However, maintaining data safety and integrity among evolving threats is becoming more and more complex and requires more stringent strategies. To avoid security hazards and […]
Challenges of Data Center Uptime and Methods of Delivering Uninterrupted Performance

Data centers are frequently called the backbones of our increasingly digitalized world, and they truly are crucial in ensuring uptime for countless businesses and applications. Demand for bandwidth keeps growing with new technologies picking up speed, and data centers rely heavily on their network infrastructure to ensure availability in a continuously changing environment. Even small […]
Edge Computing Security: Challenges and Best Practices

Edge computing involves processing data closer to where it is generated, allowing for faster processing and improved speed, which leads to greater, action-oriented results in real-time. However, edge computing security comes with inherent risks that need to be addressed. The edge computing market is estimated to be USD 15.59 billion in 2024 and growing at […]
What is Edge Networking, and How Can Companies Leverage Its Benefits?

Almost anything we do today requires, at one point or another, a specific degree of information processing and storage. Whether it’s our personal computers, appliances, or cars, there will be some amount of information manufacturers build into these devices to enhance our experience with the product. However, as users, businesses, and applications are becoming more […]
