Elevating Physical Data Center Security with Cabinet-Level Controls

In terms of preventing physical access to equipment, the cabinet is the last potential point of vulnerability in the data center. Because of this, physical data center security measures on the cabinet-level can be crucial. This can’t be stressed enough in the case of edge data centers, multi-tenant sites, or any kind of remote environment […]
Reducing the Risks of Power Outages in Data Centers

If we want to assess some of the biggest risks to data safety and continuity of digital services, the first thing that comes to mind is power outages in data centers. These disruptions can be responsible for substantial financial losses for businesses, topped up with data corruption risks and the costly downtime of critical applications. […]
What Are the Benefits of Managed Colocation vs. Traditional Colocation

Space is just one element in the equation when it comes to the spectrum of solutions and offers colocation data centers provide today. A wide variety of colocation managed services are also made available by some of these facilities, completing the colocation offer with something more. These services can assist customers with taking care of […]
Managed Services from Your Colocation Provider

A smoothly functioning IT infrastructure is one of the most fundamental prerequisites of a successful company. All businesses – regardless of their size – depend on their IT groundwork to be efficient and productive. In today’s world, where sophisticated new technologies bring a lot of change and require flexibility to adapt and keep pace, operating […]
How Real-Time Server Monitoring Can Help Your Network Servers
Servers are crucial units of all IT frameworks, and as such, they require special care and regular maintenance. Any kind of server dysfunction can create performance issues, affecting the user and leading to interruptions in workflows. Servers store and process large amounts of information with the purpose of providing it to users, applications, or other […]
Planned vs. Unplanned Downtime: What’s the Difference?

Downtime is bad for business. It is disruptive, costly, and unacceptable in today’s super-competitive business landscape. Whether scheduled maintenance or unexpected outage, being unable to access your systems during working hours can lead to productivity losses, missed opportunities, data loss, damage to your brand, and hefty Service Level Agreement (SLA) payouts. Still, you can curtail […]
Smart Hands Cost-Benefit Analysis

Imagine the following scenario. Late into the night, you receive an alert that a critical part of your server infrastructure has gone down, and the problem requires immediate attention. As a result, your e-commerce platform is no longer working, and customers around the world cannot purchase your products or services. The downtime for servers costs […]
Real-Time Server Monitoring Advantages and Benefits
As essential tools of the IT industry, both physical and cloud computing servers remain delicate, sometimes unpredictable, and often criminally underused. The data they generate, when collected and analyzed, can provide a wealth of useful information. However, server maintenance and data analysis both require dedicated monitoring, tracking, and storage. How can an IT manager balance those […]
Managed vs. Unmanaged Servers: Which is Right for Your Business?

Getting a server for your business is a significant step, but a rewarding one. The ability to host your own site or store your private data onsite, along with uninterrupted access and analysis of trends, makes this a wise investment. However, one of the first decisions you will be required to confront is whether you […]
Vulnerability Assessment vs. Penetration Test
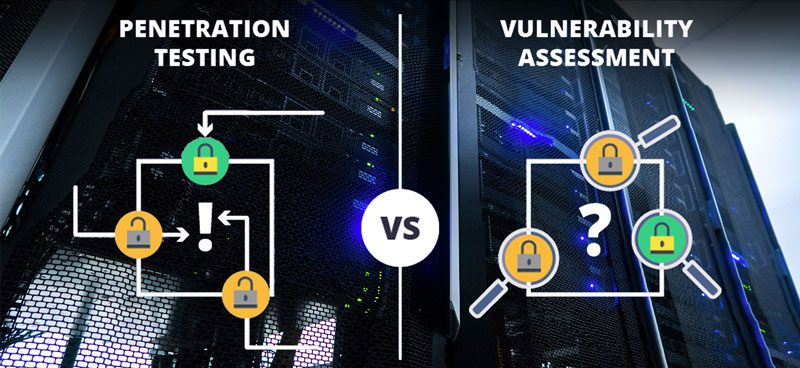
It is quite a common problem to pay for network penetration testing services and getting a hundred pages penetration testing report listing the vulnerabilities detected by a scanning tool. Vulnerability assessments are often offered in place of penetration tests. But what is the difference? Vulnerability Assessment A vulnerability assessment intends to identify certain weaknesses in […]
